In today's rapidly evolving digital world, cybersecurity has never been more important. With the continuous rise in cyber risks and advanced attacks, businesses are faced with the challenge of adapting their cybersecurity measures to safeguard their crucial data, infrastructure, and systems. The shift towards digital transformation and cloud adoption, along with the increasing complexities of cyber risks, has prompted organizations all around the world to start on a journey of transforming cybersecurity.
According to the reports, 99% of organizations plan to increase their cybersecurity budget in 2025. Why? Let’s have a deep look into this:
The rise of the remote workforce, the widespread use of cloud technologies, and the expanding attack surface have made cybersecurity a top priority for organizations across various sectors. According to recent surveys, 90% of enterprises have reported increased efforts to apply more robust cybersecurity strategies due to the rise of remote work and the increased dependence on cloud-based solutions during the COVID-19 pandemic. As a result, organizations are more focused on Digital Security Modernization to combat emerging cyber risks.
Transforming cybersecurity is not just about ticking a checkbox; it is a necessity for organizations looking to stay ahead of cybercriminals and secure business continuity in the face of ever-evolving threats. By adopting a proactive approach to cyber risk handling and embracing advanced cloud protection solutions, businesses can effectively address vulnerabilities in their digital environment and stay resilient against cyberattacks.
These numbers show the growing importance of cybersecurity in 2025, where the risks associated with digital transformation are pushing organizations to rethink their approach to cybersecurity and data protection.
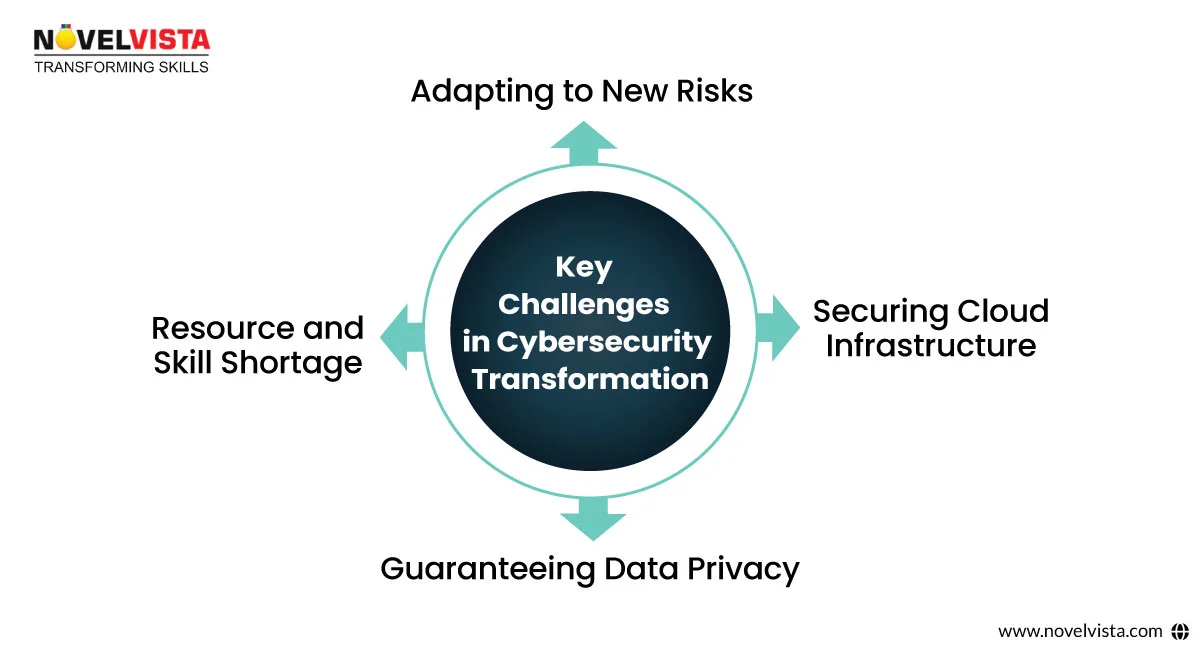
Transforming cybersecurity in 2025 isn't just about upgrading security tools—it's about a combined approach to protecting the entire digital ecosystem. Organizations are now tasked with ensuring that every layer of their digital infrastructure is protected, from endpoints to cloud environments. Some of the key challenges businesses are facing during this transformation include:
As organizations continue to expand their digital footprint, managing cyber risk has become more complex. Cyber risk management refers to the identification, evaluation, and mitigation of possible risks that could impact an organization’s digital infrastructure and data. This is especially critical as businesses embrace Digital Transformation Security strategies, where the integration of digital technologies is coupled with the need to secure the resulting data and infrastructure.
To resolve these risks effectively, organizations are implementing advanced cyber risk controlling practices, including the use of risk assessment tools, penetration testing, security gap scanning, and threat intelligence. In fact, 70% of businesses now perform regular risk assessments as part of their cybersecurity strategy. By doing so, they can better understand the specific risks associated with their digital transformation initiatives and take proactive steps to reduce possible threats before they materialize.
Moreover, businesses are increasingly relying on cyber risk handling tools to ensure compliance with data protection regulations such as GDPR, HIPAA, and CCPA. These regulations require organizations to implement strict security measures to protect personal data, and failing to comply can result in multiple financial and reputational damages. As such, aligning cybersecurity strategies with compliance requirements is a crucial component of any transformation journey in cybersecurity.
One of the most significant aspects of the transformation of cybersecurity in 2025 is the growing reliance on cloud security solutions. With the increasing migration of workloads and sensitive data to the cloud, businesses must rethink their security posture to adapt to this new model.
Cloud environments are commonly seen as more secure than traditional on-premise infrastructures, but they come with their own set of vulnerabilities. The shared responsibility model in cloud security requires organizations to manage their own security controls while relying on cloud providers for the infrastructure. This creates a need for a new approach to Digital Security Modernization—one that includes a combination of robust cloud security measures, real-time threat monitoring, and proactive risk management strategies.
Cloud protecting solutions like encryption, access control, identity and access management (IAM), and multi-factor authentication (MFA) are now essential components of a comprehensive cybersecurity strategy. The adoption of these solutions is growing rapidly, with 57% of enterprises prioritizing cloud security as a part of their overall IT modernization efforts.
Organizations are also using these tools to improve their Risk Management strategies, making sure that any vulnerabilities in their cloud environment are quickly addressed before they can be exploited.
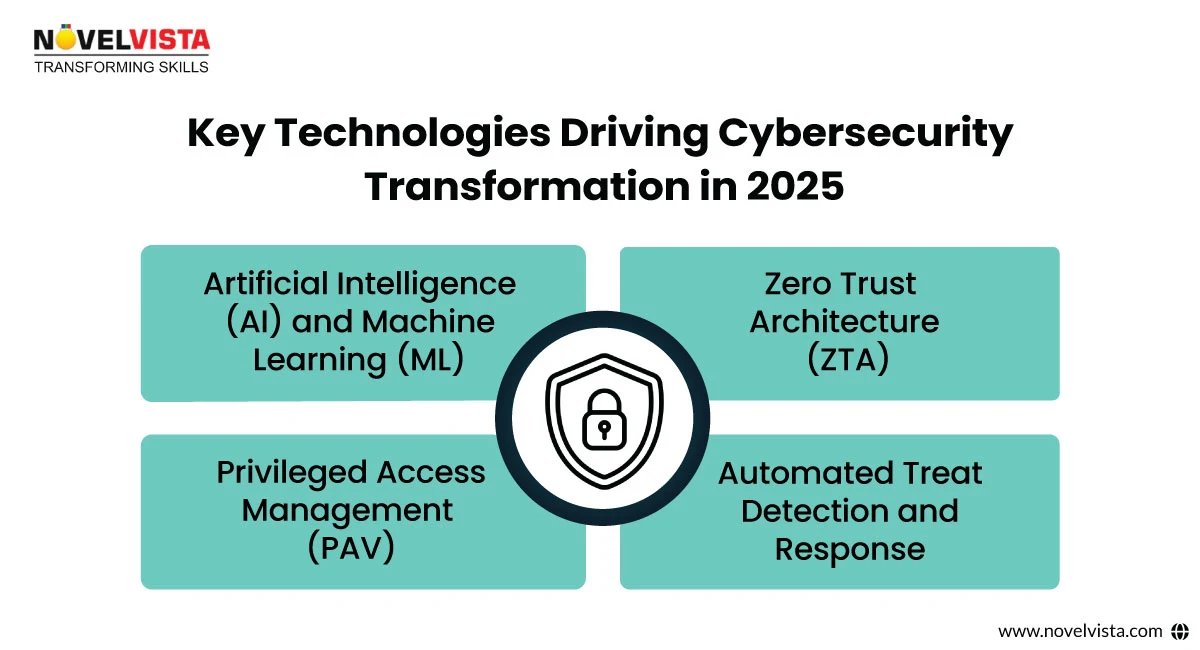
In 2025, several key technologies are ready to drive the next wave of transformation in cybersecurity. These technologies help organizations improve their security operations and manage the growing complexities of cyber risks:
The next wave of cybersecurity change is focused on the combination of advanced technologies like artificial intelligence (AI), machine learning (ML), and automation to improve security operations. These technologies allow organizations to identify and respond to risks in real-time, making cybersecurity operations more effective and improved.
Moreover, businesses are increasingly investing in Digital Transformation Security solutions that combine security directly with the design and development of their digital initiatives. This proactive approach makes sure that security is built into the fabric of digital transformation, rather than being an afterthough
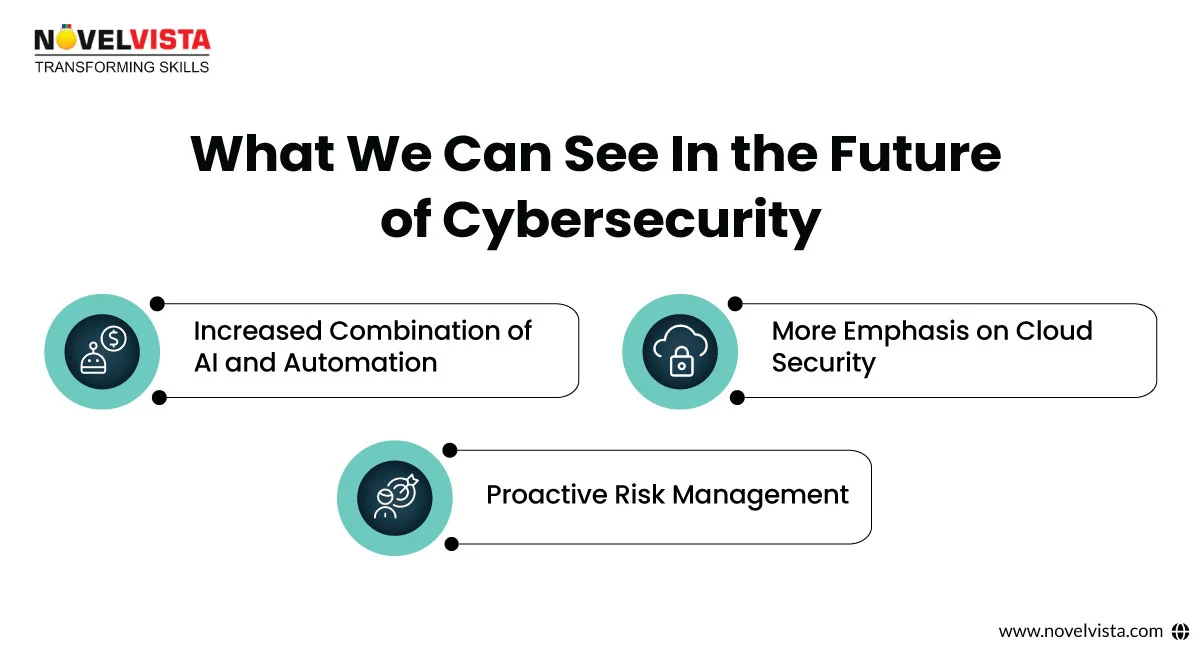
As we look toward the future, the need for transforming cybersecurity will continue to grow. With the increasing advancement of cyberattacks and the expanding threat area, organizations must prioritize cybersecurity as part of their long-term strategy. The digital world is evolving at a rapid pace, and cybersecurity must evolve alongside it.
In 2025 and beyond, we can expect to see:
For businesses looking to stay ahead of the curve, investing in Cybersecurity Transformation initiatives is not just an option—it's an imperative.
In conclusion, the landscape of cybersecurity is transforming at a rapid pace, and organizations must adapt to these changes to stay protected. By putting money in Digital Security Modernization, adopting cloud security practices, and implementing effective cyber risk management strategies, businesses can mitigate the risks associated with digital transformation and position themselves for success in 2025 and beyond.
Equip yourself with the knowledge and tools to lead in a rapidly evolving digital landscape—secure your organization's future now.
Confused about our certifications?
Let Our Advisor Guide You