There's been a lot of discussion about models and consistency (ISO 27001 and GDPR to give some examples). We've been discussing these guidelines quite a bit lately. What we haven't done several deals on is the discussion about what individuals need to do to plan for these principles while guaranteeing you're consistent with the commitments you currently have.
Probably the ideal approach to get ready is to conduct a Risk Assessment for your business. We sat down with Darrin Maggy, CISSP, our Practices Manager, to audit the seven stages of a Risk Assessment.
While we've given a great effort to place these means into an organised list, a large number of them are interconnected, and when you experience a Risk Assessment, you'll be bouncing back and forth between them as new data becomes visible.
Risk analysis might sound like a hurdle, but think of it as your security GPS—helping you explore risks before they turn into harmful problems. If you're aiming for ISO 27001 compliance, a well-structured approach to identifying, evaluating, and mitigating risks is non-negotiable. In this guide, we'll take a look at everything you need to know about performing an ISO 27001 risk assessment, from frameworks and methodologies to practical solutions.
A data resource is any data or resource that is important to your business and adds to its capacity to work and its benefit. Normally, you have to search for things like paper or electronic records, applications, information bases, frameworks, and even key individuals. That is a data resource.
"By and large, what we do to begin the benefit distinguishing proof cycle is issue a survey," Maggy said. "It's brief, and it's intended to provoke individuals through the way toward seeing precisely what we're searching for and how to discover it."
After you've distinguished your data resources, Security7 figures out who inside the business is liable for those benefits. Maggy said the beneficiaries of the survey commonly exist at the layer directly underneath the CEO on the organisation chart.
"Fund, Operations, HR, Sales, and so forth, These people are regularly mindful of which corporate resources they're answerable for and which resources are generally basic to the business," he said.
Maggy said it's imperative to distinguish resource proprietors as they are the best wellspring of information concerning the possible weaknesses and dangers to the benefits, and they can likewise help evaluate the probability and effect of the recognised dangers were they to appear.
"Classification, Integrity, and Availability of data are the establishment of data security," Maggy said. "How about we utilise a similarity to help clarify this?"
Maggy said, envision you're working with your bank. You're going to make a store, sign in to your record to ensure the store has been set up for you, and afterwards pull back the cash.
You expect secrecy when you store your cash. That exchange is between you and your bank. "It's no one's business that you've recently led that exchange," Maggy said. "The bank shouldn't publicise the way that you just kept $50 or $5000 into your account."
Honesty becomes possibly the most important factor when you sign in to your record just to discover the exchange hasn't been posted. "Let's assume you saved $50 and just observe $10 or nothing by any stretch of the imagination," Maggy said. "Something's happened concerning the respectability of that exchange, the honesty of the data."
Accessibility comes about when you go to an ATM and attempt to pull back that $50, and you can't do so; presently, you have an accessibility issue."
Maggy said each of these three things applies to information, also any breach of Confidentiality, Integrity, and Availability is viewed as a security episode. "We should apply these ideas to the business.
"On the off chance that someone in deals needs to get to Salesforce.com and they're not able to do so, that is an accessibility issue. If someone from HR goes into Salesforce.com and they adjust a significant record, rolling out considerable improvements to the record, and eventually those progressions change how a customer is taken care of in the association at then you've quite recently had a breach of honesty," he said.
"Generally speaking, classification is distinguishing the cycles, the advantages, the data, the things in the association that should be kept hidden," Maggy said. Regardless of whether it's existential information that you don't need your rivals to get some answers concerning, for example, data identified with M&A movement or new product development, financial data, or other sensitive information. That is secrecy."
Recollect when we said you may bob around between the means? Indeed, here's a case of that.
"Oftentimes, we'll verify that the benefited proprietor winds up being the hazard proprietor also," Maggy said.
Maggy said hazard proprietors are those with the responsibility and position to oversee change. "The advantage proprietor is the individual responsible for the benefit within the organisation. A hazard proprietor is an individual who is both keen on settling a hazard and is situated sufficiently high in the organisation to take care of business."
Be that as it may, the hazard proprietor isn't generally the advantage proprietor. "it must be somebody who is firmly identified with cycles and tasks where the dangers have been recognized – it must be somebody who will feel the "torment" if the dangers emerge – that is, somebody who is a lot of keen on keeping such dangers from occurring. Nonetheless, this individual must be situated sufficiently high so their voice would be heard among the chiefs because without getting the assets, this undertaking would be unimaginable."
Maggy said it's critical to consistently give Risk Assessment training directly to the individuals who will be engaged in the Risk Assessment process.
"We do this to update everybody engaged with the cycle," he said. "It encourages them to comprehend the technique, the wording, and the hazard recognisable proof and treatment measure so we can more readily guarantee a high-quality, refined yield.
Security Networks has amassed an assortment of Risk Catalogues to help the members on their journey. The lists help distinguish explicit dangers and weaknesses and permit them to guide associations through the probability and outcome situations.
"We give the possible effect and probability of these dangers happening a mathematical incentive in our hazard grid."
All of these qualities eventually help figure out which dangers will require treatment.
"At that point, you need to conclude how you will decrease those dangers to a level that the association is happy to acknowledge or is OK with, no more, no less," he said.
The essential hazard treatment alternatives an association needs to consider are risk mitigation, risk transfer, risk avoidance, and risk acknowledgment.
"Possibly you're going to set up a security control from Annexe A or SP 800-153, or another control inventory. That is hazard relief," Maggy said.
"Hazard move is the point at which you move the hazard through redistributing to an agreement provider or safeguarding a specific resource."
"Hazard evasion is the point at which you end the movement that is related to the hazard," he said.
"Hazard acknowledgement is the point where an organisation says, 'You recognise what?' The treatment would cost more than the potential effect was the hazard were to emerge. We acknowledge this hazard. It's been approved by our leadership suite," he said. "At that point, they record the hazard acknowledgement reminder inside their data security management framework"
Imagine building a castle without knowing where attackers might strike. That’s what handling information security risk without a plan looks like. A proper risk evaluation helps businesses identify weaknesses, prioritize risks, and apply security controls to secure important assets.
Without a structured risk assessment, organizations expose themselves to cyber threats, data breaches, and compliance failures. Whether you’re a security professional or want to be an ISO 27001 Lead Auditor Certification holder, mastering risk assessment is a must.
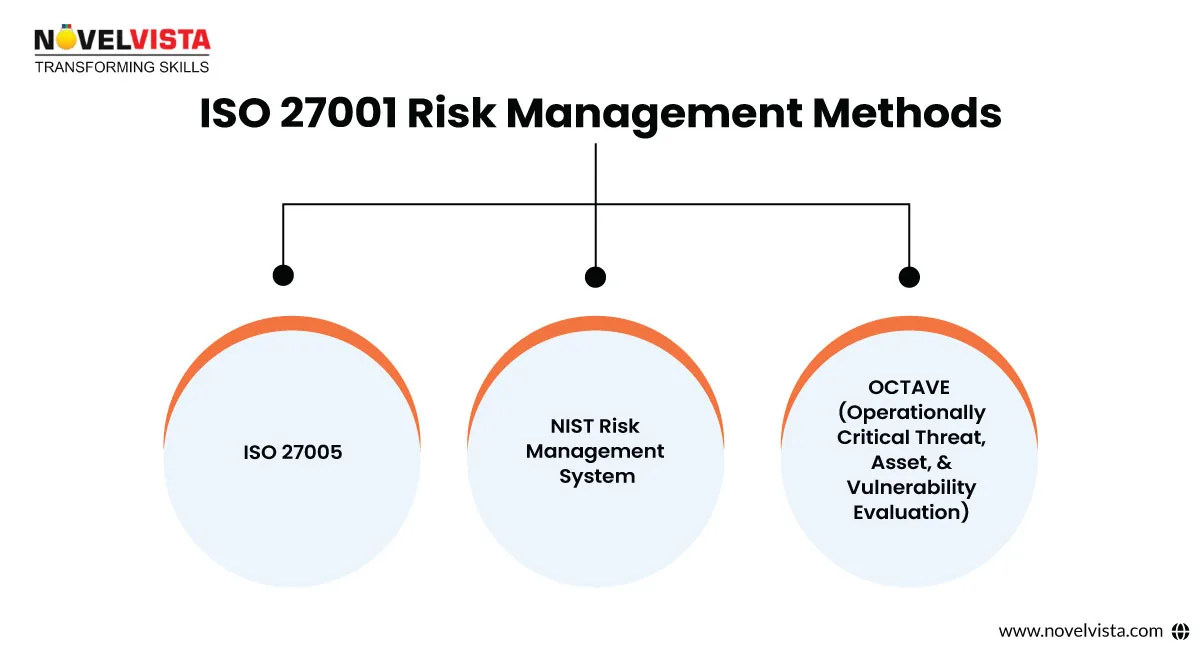
Risk management isn’t a one-size-fits-all approach. Different businesses follow different risk management systems, but ISO 27001 provides a planned way to tackle protection. Some widely used methodologies include:
Not all risks deserve the same level of attention. Some could be extremely harmful, while others are small annoyances. Here’s how to categorise them:
A strong ISO 27001 risk analysis ensures your organisation tackles the most pressing security threats before they escalate.
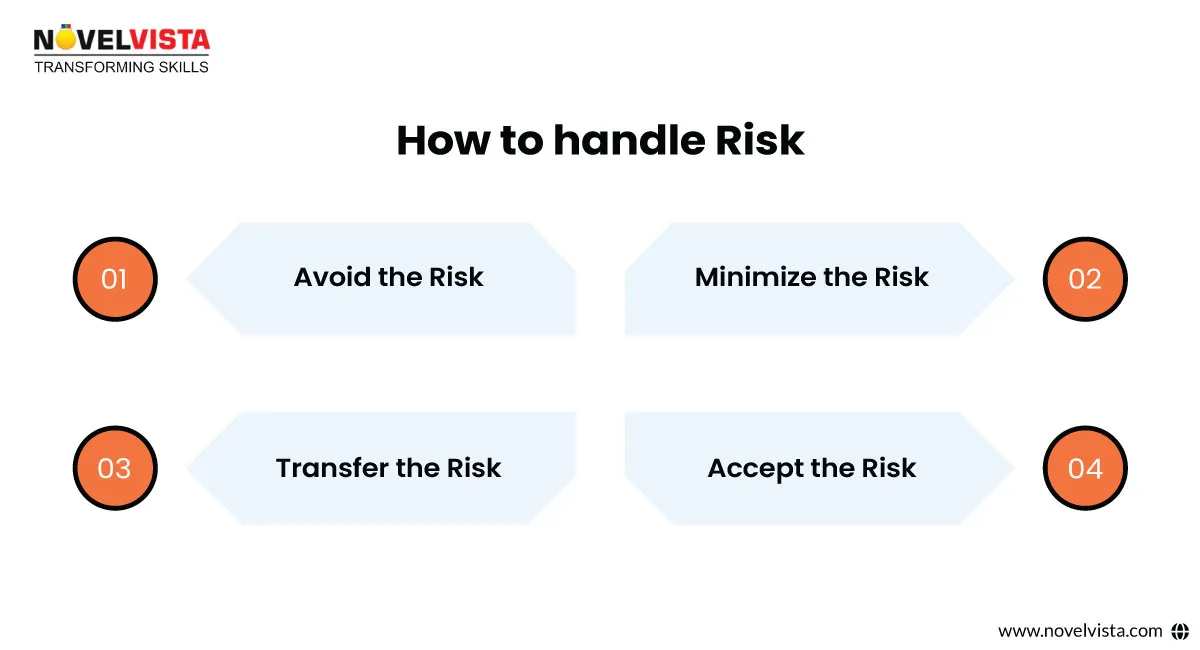
Once you've identified risks, it’s time to decide how to handle them. ISO 27001 explains four primary risk treatment options:
Each organization must decide which method matches best with its business objectives and ISO 27001 compliance goals.
Proper documentation is critical for both internal security management and ISO 27001 audits. Here are the essential risk assessment documents:
Organizations aiming for certification should also budget for training. Check out the ISO 27001 Certification Cost to get a clear picture of compliance-related expenses.
Performing a risk assessment does not always follow a straight path. Many organizations face difficulties with common roadblocks, such as:
1. Challenge: Lack of stakeholder involvement
2. Challenge: Unclear risk prioritization
3. Challenge: Keeping up with evolving threats
To understand risk assessment from a business perspective, explore ISO 27001 for Businesses—a must-read for organizations working on compliance.
A risk analysis isn’t a one-time project—it’s an ongoing process. It should be fully combined into your Information Security Management System (ISMS) and improve as your business grows. Regular assessments ensure that new risks are identified and addressed before they pose serious threats.
Businesses serious about compliance should invest in professional training. The ISO 27001 Lead Auditor Certification provides security professionals with the skills to perform risk evaluation, audits, and compliance analysis.
Discover the 7 essential steps to identify, evaluate, and treat risks effectively.
Threat assessment might seem difficult, but with the right methods, it becomes a powerful tool for protecting your organization. By following structured techniques, prioritizing threats, and combining risk analysis into your ISMS, you’ll be well on your way to achieving ISO 27001 compliance.
Want to polish your skills? Visit NovelVista for expert-led training and resources to help you master information security.
Confused about our certifications?
Let Our Advisor Guide You