Businesses face previously unheard-of cybersecurity issues in today's fast-paced digital world, when every click, transaction, and conversation invariably involves sending sensitive data. Escalating sophistication of cyber threats along with growing scrutiny from regulating bodies has made robust information security practices non-negotiable. The internationally recognized standard for ISMS, namely ISO 27001, has emerged as a cornerstone for businesses that want to safeguard their data and maintain trust among stakeholders.
This blog explores why ISO 27001 is important in the modern cybersecurity landscape, including the pros of implementation, the steps to implement, and its role in furthering digital resilience.
The digital landscape is perpetually changing, and so are the cyber threats. Advanced ransomware, phishing attacks, and social engineering can now target vulnerabilities within organizational systems, infrastructure, and human behavior.
Beyond the financial loss, consequences of such attacks include regulatory penalties, operational disruptions, and eroded trust among clients and partners. According to IBM’s Cost of a Data Breach Report 2023, the average cost of a data breach in 2023 was USD $4.45 million, a 2.3% increase from 2022’s cost of $4.35 million. In these regards, ISO 27001 works as a proactive measure to help an organization mitigate risks before they escalate.
The International Organization for Standardization (ISO) developed the information security standard ISO 27001, formally known as ISO/IEC 27001:2022, which offers a structure and principles for creating, putting into practice, and overseeing an information security management system. ISO 27001 is considered to be a part of the ISO/IEC 27000 family of standards dealing with information security. It offers a comprehensive framework for information protection using a risk-based approach. The standard encompasses policies, procedures, and controls that address potential vulnerabilities to facilitate the confidentiality, integrity, and availability of organizational data.
Unlike 'piecemeal security', the ISO 27001 approach brings about security within the organizational culture. Being a process-driven approach, it makes it flexible and scalable, and businesses of all shapes and sizes and across all industry sectors can implement the standard.
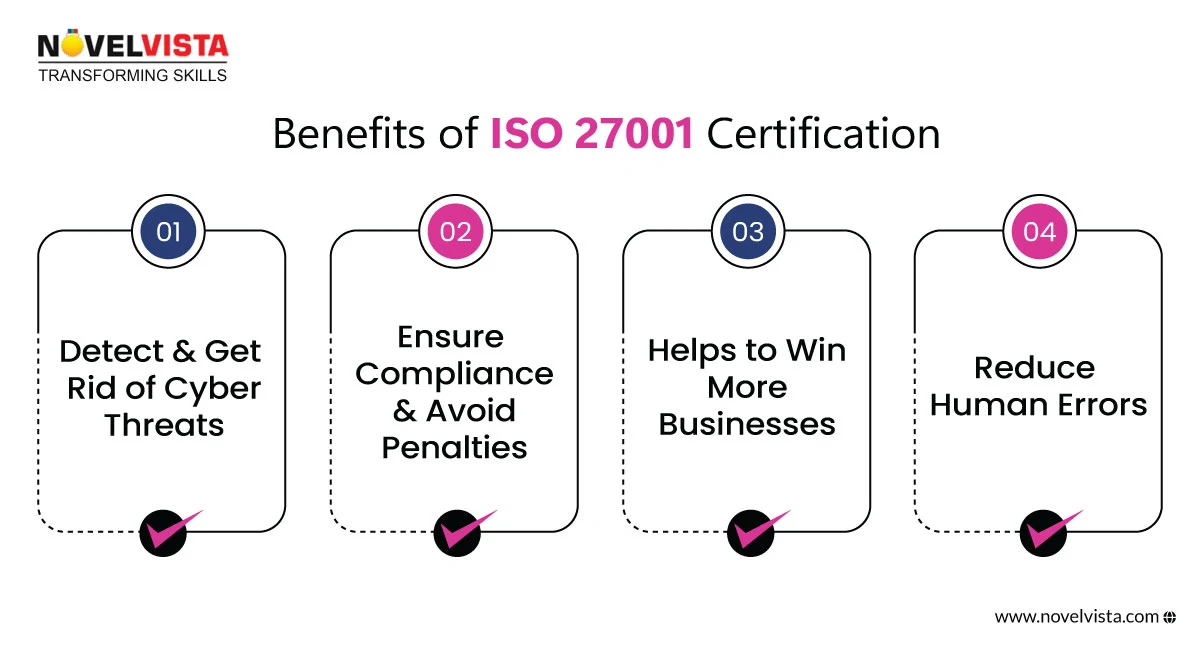
Cyberattacks are becoming more complex and targeting organisations of all sizes. ISO 27001 offers a structured approach to handling security threats by implementing Controls and Policies that safeguard critical assets.
Make your cybersecurity posture stronger. Understand more about ISO 27001 Risk Assessment.
In an era of GDPR, HIPAA, and other data privacy laws, businesses can no longer afford to overlook Data Protection Compliance. Failure to comply can lead to massive penalties, legal actions, and reputational damage.
ISO 27001 helps businesses stay compliant while building a security-first culture.
Want to ensure compliance? Explore how ISO 27001 Data Protection can help safeguard your organisation.
ISO 27001 certification is about security and business growth. Many organisations only work with certified vendors, making it an instant trust signal.
Need proof? Companies that adopt ISO 27001 have seen higher client retention rates and improved business opportunities.
Learn about the business impact of security compliance with Information Security Management Benefits.
Human error can compromise even the most advanced cybersecurity systems. ISO 27001 helps organisations train employees, implement strict ISO 27001 Controls and Policies, and create a culture of security awareness.
Want to implement the best security measures? Start your journey with ISO 27001 Lead Auditor Certification Training.
ISO 27001 is often compared with other security frameworks, for example, NIST and COBIT. While all of them are worth discussing, ISO 27001 has always had a cut over competitors in terms of its global recognition, a comprehensive risk-based approach, and the "Continuous Improvement" stipulation. It can be applied across almost every kind of industry or sizes of organizations.
A structured procedure that integrates security into every sector of an organization's operations is necessary for ISO 27001 certification. Usually, the procedure consists of:
Although obtaining certification takes work, the long-term advantages greatly exceed the initial process.
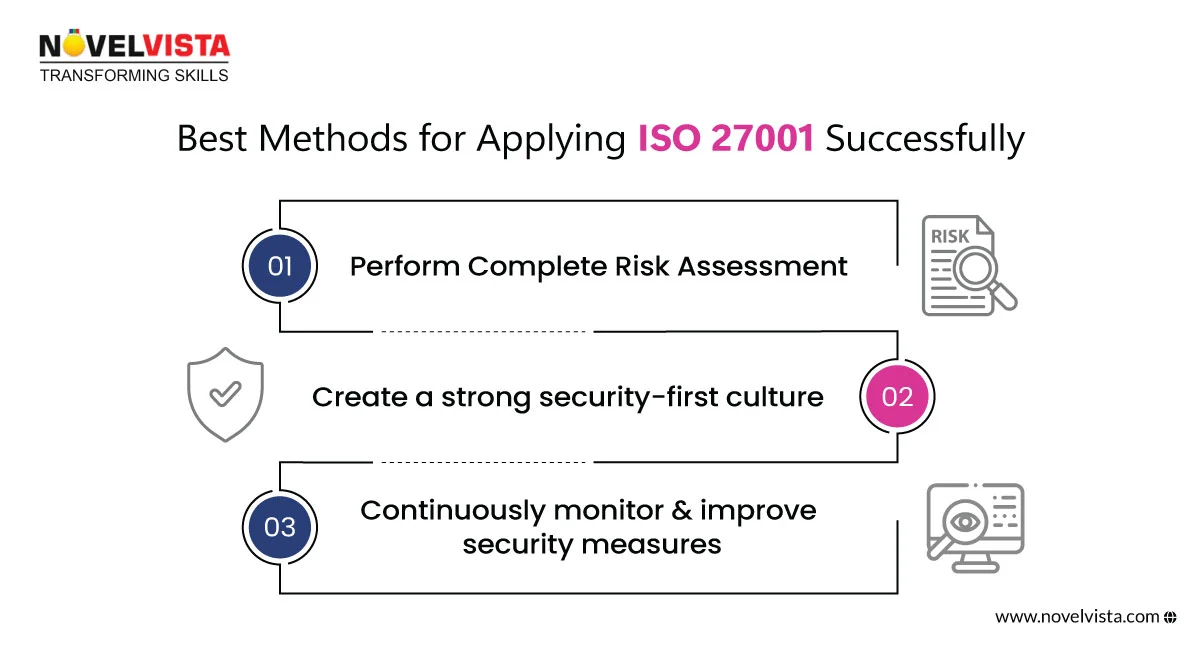
ISO 27001 application needs careful strategy and constant Execution. Here are three key best practices for a seamless deployment process:
Before implementing ISO 27001, businesses must conduct an Information Security Risk Assessment to identify critical potholes and focus on security procedures.
Need expert guidance? Learn more about ISO 27001 Risk Assessment.
ISO 27001 is not only about getting certified but also about managing long-term security resilience.
Ready to future-proof your security strategy? Start with ISO 27001 Lead Auditor Certification Training.
By now, it's clear that the benefits of ISO 27001 don't stop at just security - they run business success. However, how does this work in real-world scenarios? Let's evaluate how companies have applied the ISO 27001 Certification to strengthen their data protection compliance and reduce cyber threats.
Industry: Financial Services
Challenge: Struggled with increasing cyber threats and inconsistent security policies.
Solution: Applied ISO 27001 Controls and Policies to make their risk management stronger and upskill employees on Cybersecurity Best Practices.
Results:
Want to implement a structured risk framework? Check out how the Adoption of ISO 27001 can help your business.
Industry: Healthcare
Challenge: Needed to comply with HIPAA regulations and secure sensitive patient data.
Solution: Integrated ISO 27001 Certification Benefits by enforcing access control, encryption, and internal security audits.
Results:
Searching for compliance solutions? Look at how ISO Audit in Public Sector can help organisations satisfy regulatory standards.
A mid-sized financial services company implemented ISO 27001 to comply with regulatory requirements and enhance client trust. Within two years, the organization reported a 30% reduction in security incidents and a 15% increase in client retention due to improved confidence in their data protection measures.
A healthcare provider, which handled confidential patient information, complained about difficulties in maintaining compliance with the HIPAA standard. Through adopting ISO 27001, the provider streamlined its security practices and ensured compliance with HIPAA regulations as well as protecting patient information from unauthorized access.
By adjusting to new issues like cyberattacks powered by artificial intelligence (AI) and the Internet of Things (IoT), ISO 27001 continues to stay relevant as the digital world changes. The standard's focus on flexibility guarantees that businesses can successfully handle these emerging risks.
With increasingly advanced cyber threats, businesses can't afford to overlook security. ISO 27001's benefits don't stop at compliance; they go beyond it. It encourages businesses to actively protect data, build trust, and stay ahead of evolving threats.
The time to strengthen your security strategy is NOW. Don’t wait for a cyberattack to take action!
Stay ahead of the game with ISO 27001 certification!
With the help of the above details, it can be easily understood that ISO 27001 is more than just a compliance requirement in today’s strategic imperative businesses. Its approach performed for stakeholders to gain their trust, regulatory compliance, and risk management provides businesses a strong barrier against online attacks. For businesses which are trying to succeed in the digital era, ISO 27001 is more than preventing threats or breaches, it's also about creating a culture of security and maintaining long-term resilience. Businesses also gain confidence in handling the complexities by using this standard.
Confused about our certifications?
Let Our Advisor Guide You