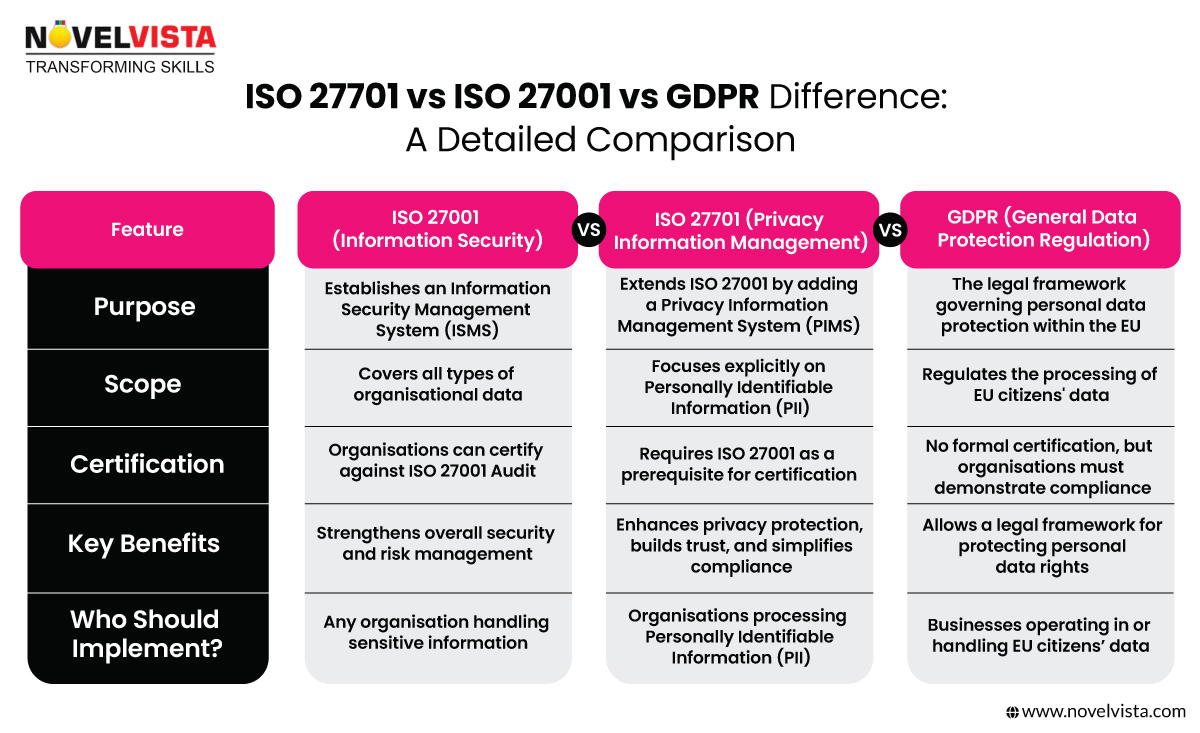
Protecting info is critical nowadays. ISO 27001 defines procedures for establishing secure systems that safeguard vital data. Earning this certification indicates an organization prioritizes clients' privacy.
Having achieved this allows firms to better shield sensitive details from unauthorized access.
However, ISO 27701 expands beyond 27001's scope - it outlines management guidelines for personal data specifically.
This facilitates legal compliance concerning privacy regulations such as GDPR within EU nations. Jointly implementing these standardized practices assures stakeholders the entity takes data security extremely seriously.
The ISO 27000 series intends to defend organizations against cyber threats through robust information security management.
Attaining 27701 credential, coupled with relevant training programs, bolsters existing defenses.
Aligning with international norms regarding personal data practices further strengthens privacy protections.
This goal helps meet data privacy regulations - a key reason to grasp ISO 27001 and ISO 27701 distinctions for cyber compliance excellence.
ISO 27001 provides a robust framework for managing and protecting sensitive organizational information. Here’s an overview of its key components:
This structure supports organizations in building a culture of security and continuously improving their security posture.
Obtaining ISO 27001 certification, combined with industry-recognized certifications like theISO 27001 training and certification, demonstrates an organization's comprehensive commitment to information security.
ISO 27701 serves as a pivotal extension to ISO 27001, focusing specifically on privacy management pertaining to Personally Identifiable Information (PII).
Here’s an overview of its key components:
This standard not only complements the existing ISMS but also ensures a robust approach towards privacy management, aligning with global regulatory requirements.
ISO 27001 and ISO 27701 work together. While ISO 27001 compliance ensures the protection of all types of information, ISO 27701 specifically focuses on privacy and personal data protection. Think of ISO 27001 as the security system and ISO 27701 as the privacy lock that safeguards personal data.
Organisations that already have ISO 27001 can quickly expand their security architecture to incorporate privacy management. This makes it much easier to comply with GDPR, CCPA, and HIPAA without starting from scratch. By combining both, companies demonstrate their commitment to securing both business and customer data, strengthening trust with clients and partners.
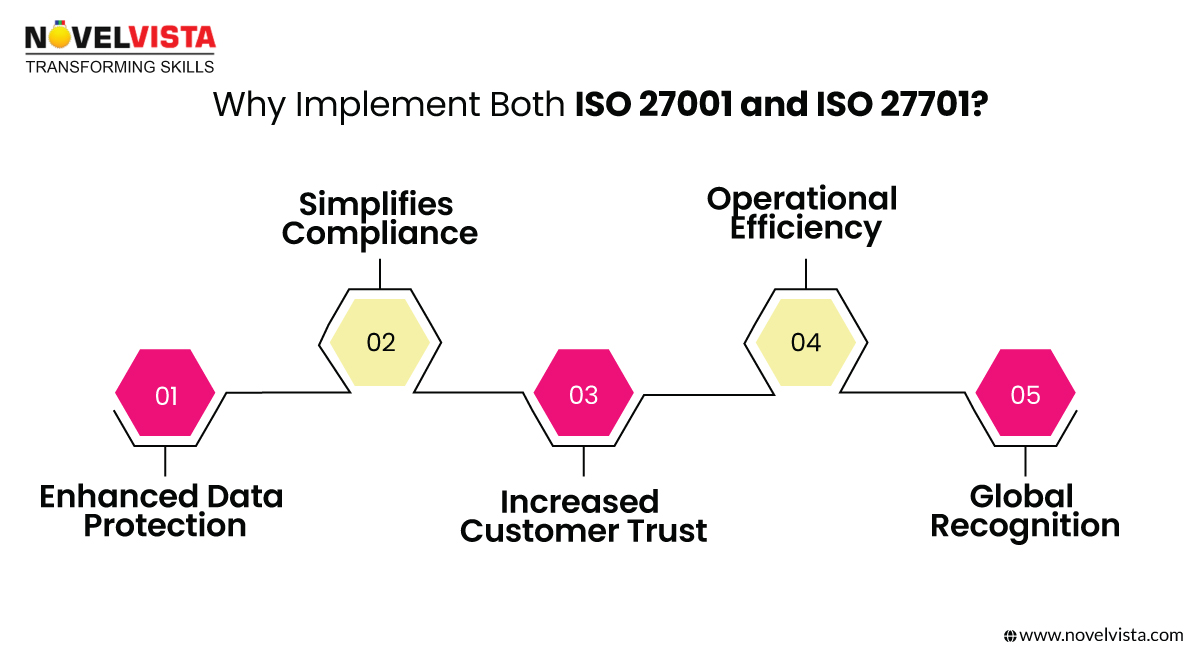
Adopting both standards provides a significant competitive advantage:
1. Enhanced Data Protection – Strengthens cybersecurity and ISO 27701 vs 27001 controls, reducing the risk of data breaches.
2. Simplified Compliance – Helps meet regulations like GDPR, CCPA, and HIPAA effortlessly.
3. Increased Customer Trust – Shows clients, partners, and regulators that data privacy is a top priority.
4. Operational Efficiency – Integrating both frameworks simplifies privacy and security processes, eliminating redundancy.
5. Global Recognition – These certifications are respected worldwide, making international expansion smoother.
In short, adopting ISO 27001 and ISO 27701 isn’t just about compliance—it future-proofs your organization.
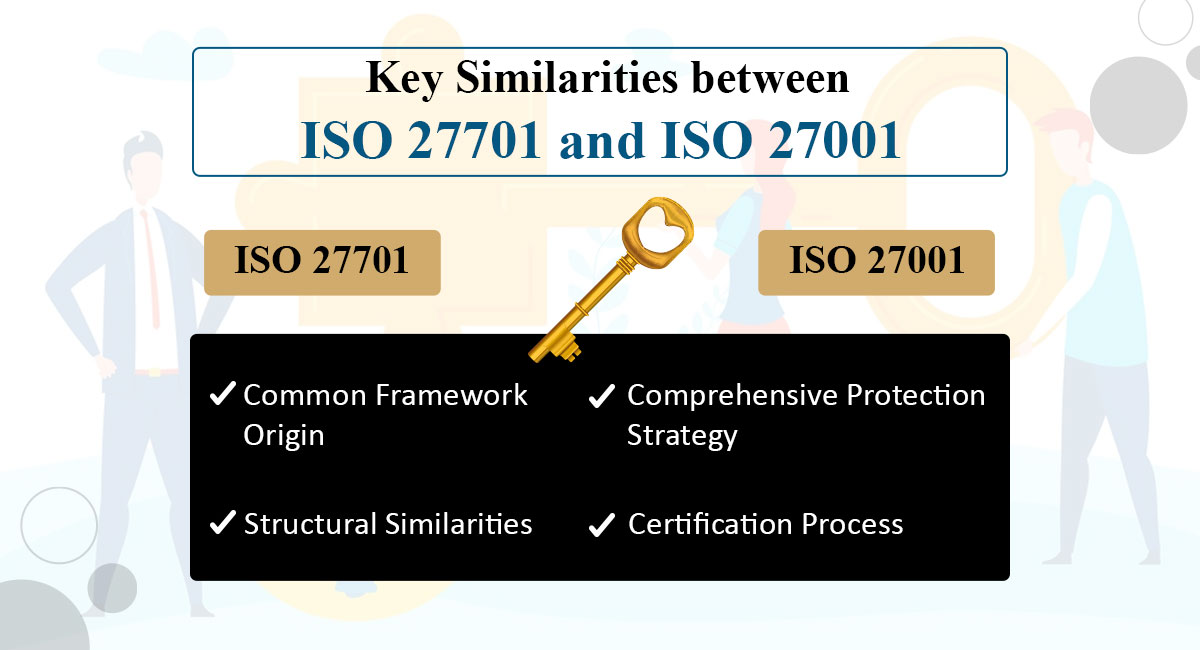
ISO 27701 is not a standalone certification but an extension of ISO 27001. This means that organizations must first be compliant with or certified in ISO 27001 before they can pursue ISO 27701 certification.
It is mandatory for an organization to be ISO 27001 compliant in order to qualify for ISO 27701 certification.
This underscores the foundational role that ISO 27001 plays in establishing the necessary information security management systems before an organization can enhance its privacy management through ISO 27701 as stated bysitegraph.
These distinctions highlight the interdependency and the structured progression from ISO 27001 to ISO 27701, emphasizing the layered approach to managing information security and privacy.
Simplifying this process involves breaking the documentation into manageable parts and possibly outsourcing some of the record-keeping tasks.
Methodologies like Six Sigma, Agile, Lean, PDCA, Kaizen, and Total Quality Management, coupled with technical certifications such as theNV certification and training, can be instrumental in fostering a culture of continuous improvement

To foster continuous improvement, methodologies like Six Sigma, Agile, Lean, PDCA, Kaizen, and Total Quality Management can be instrumental.
ISO 27701 and ISO 27001 are important certifications. They help organizations keep information secure and private.
To get certified, organizations must follow detailed rules. This shows they value data security and privacy.
ISO 27001 focuses on information security.ISO 27701deals with privacy information too.
Together, these certifications give a plan for protecting data. They help organizations follow privacy laws. Understanding the differences between ISO 27001 and ISO 27701 is key. It shows how they build on each other to improve data protection.
Combining ISO 27701 with ISO 27001 has major effects beyond just following rules. Organizations gain an advantage in the digital market, where trust and security matter a lot.
Aligning with global privacy laws and preparing for future regulations strengthens an organization's reputation, efficiency, and strategic position.
As businesses navigate the constantly changing worlds of information security and data privacy, adopting these standards not only reduces risks but also paves the way for improving privacy management practices continuously.
This suggests more research and action are needed for excellent cybersecurity governance.
Thank you for reading!
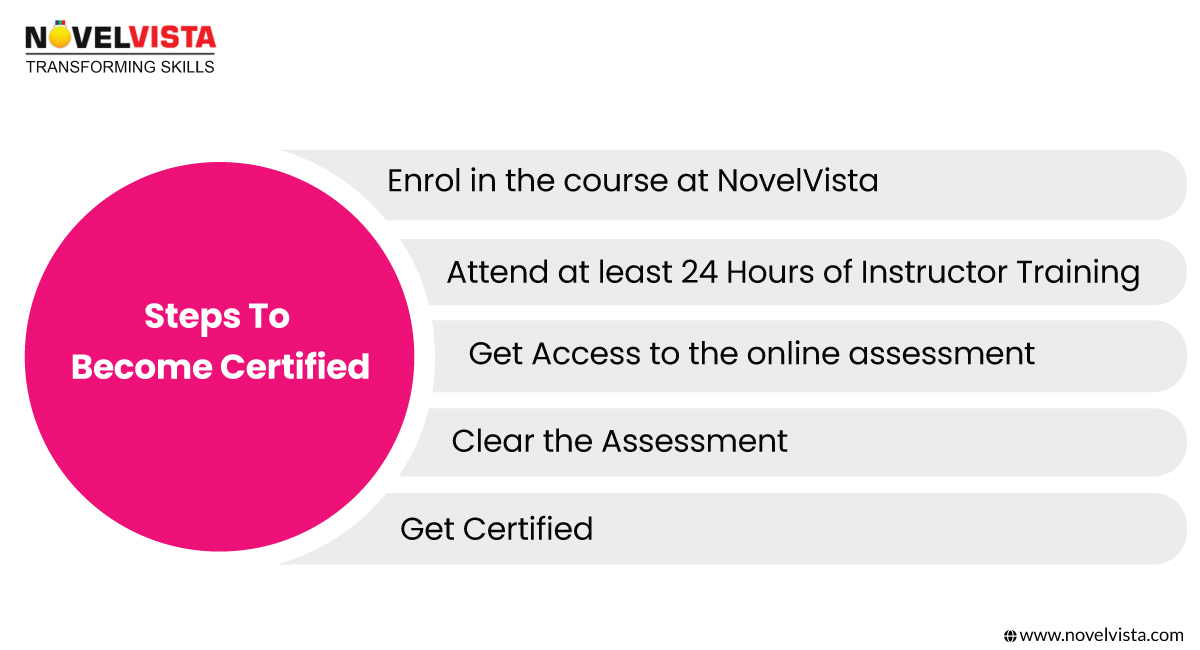
Use these organized procedures to guarantee a seamless and quick certification process if you wish ISO 27001 and ISO 27701 certifications:
1. Enrol in the Course at NovelVista – First register for either ISO 27001 Certification Training or ISO 27701 Lead Auditor Training. These courses help you develop knowledge in information security and privacy management by delving deeply into ISO 27001 compliance and ISO 27701 requirements.
2. Attend at least 24+ Hours of Instructor Training – Gain practical knowledge in risk management, security controls, and ISO 27701 vs 27001 compliance. Real-world applications and practical case studies guarantee your grasp of how to apply these criteria successfully.
3. Get Access to the Online Assessment – Following completion of the program, you will be able to access the official certification exam online. This test evaluates your knowledge of security systems, ISO 27001 audit procedures, and ISO 27701 vs 27001 controls required for compliance.
4. Clear the Assessment – Successful passing of the assessment confirms your capacity to control privacy frameworks and information security concerns. It shows your knowledge of putting in place and preserving an ISO-certified management system inside a company.
5. Get Certification – Once you pass the exam, you will be industry-recognized certified in ISO 27001 and ISO 27701, therefore proving your capacity to control security and privacy issues properly. This certification helps companies satisfy worldwide compliance and security criteria and increases job prospects.
Take the first step to your skill upgradation! Enrol in ISO 27001 Certification Training or ISO 27701 Lead Auditor Training to progress your knowledge of information security and privacy management.
Important Note:You cannot obtain ISO 27701 certification without first obtaining ISO 27001 certification, as privacy management builds upon information security.
In today’s evolving digital landscape, organizations must proactively approach security and privacy. ISO 27001 ensures robust information security, while ISO 27701 extends this framework to cover privacy management, making compliance with regulations like GDPR, CCPA, and HIPAA seamless.
By implementing both standards, businesses can enhance cybersecurity, streamline compliance, build customer trust, and gain a competitive advantage. Certification is not just about meeting legal requirements—it’s about future-proofing your organisation in an era where data protection is critical.
Ready to strengthen your security and privacy framework? Start your journey with ISO 27001 Certification Trainingand ISO 27701 Lead Auditor Trainingat NovelVistatoday!Confused about our certifications?
Let Our Advisor Guide You