Technology has thrived at break neck speed in the previous decade. Developments and advancements have changed the way we live and work. We live in an interconnected reality where everything is on the web. While this has made our lives simpler, it has likewise made us helpless against modern cybercriminals, who at their malicious best attacks a person as well as even an organization, and in more audacious attacks even a country's security and monetary wellbeing.
As per the most recent report by Verizon, 70% of cybercrimes were brought about by malignant programmers and outcasts. With a ton of delicate information currently being available on the web, the discernment danger has consistently developed throughout the long term.
One of the chief strategies to forestall cybercrime is to fortify the security of IT frameworks. Besides, adding a devoted group of ethical hackers to the labor force can help fix provisos and forestall malicious hackers. With the flood in cybercrime, the requirement for network protection has expanded. This thusly has prompted an ascent in the interest for gifted ethical hackers and data security experts.
Certified Ethical Hacking course is specially designed to take the data security experts to the core of ethical hacking. Certified Ethical Hacker (CEH) is a qualification obtained by demonstrating knowledge of assessing the security of computer systems by looking for weaknesses and vulnerabilities in target systems, using the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system.
By taking this certification course, you will learn all about:
As indicated by Forbes, "in this current year of 2020-21, the Global security market is worth $173 billion and inside the following 5 years this will develop to around $270 billion." Statistics by the Australian Cyber Security Growth Network show that associations over the globe are relied upon to raise their security spending plan by 8% every year.
Malicious Cyber Activities are expanding far and wide, as cybercriminals are utilizing complex methodologies for penetration of frameworks and organizations. Thusly, the interest for network protection specialists or ethical hackers will keep on expanding.
In India alone, in excess of 20,000 sites confronted defacement, DDoS, or ransomware attacks simply in 2019 according to the report of CERT(Indian Computer Emergency Response Team).
Consequently, from private associations to government elements, everybody needs an ethical hacker or security expert to counter unapproved hacking and reinforce their security needs. According to the NASSCOM report, there will be at least 72000 security expert job openings per month across the globe in the coming years.
Cybersecurity specialists will get different kinds of job openings from small scale associations to monster tech partnerships, government offices, research associations, and numerous others.
Their job responsibility will vary and isn't restricted to the size and necessity of the association, yet additionally the aptitudes and experience of
hackers. Notwithstanding, here are some general obligations anticipated from moral programmers.
To play out all the above assignments and activities there are various designations recruited by associations, going from passage level security staff to CISO (Chief Information Security Officer). This pyramid shows the different degrees of functions for network safety experts.
Below are some areas where Ethical Hackers are heavily needed:
Worthwhile pay rates are the most appealing piece of this calling. Compensations in this field change dependent on the spot, assignment, ability, and experience. As we have found in the pyramid before, there are various functions in the security field, with bundles expanding from base to top. All associations esteem their security and are prepared to pay as much as possible for qualified competitors.
According to an overview, the normal compensation of an ethical hacker or data security official is INR 12,00,000 for every annum with 3-5 years of involvement. This is only a normal figure. Now and again in New Delhi and Mumbai, reasonable competitors got paid as much as up to INR 18,00,000 p.a. indeed, even without work insight.
The bundle data referenced above was only for India. How about we examine the underneath table to comprehend the overall compensation proportion dependent on assignment and experience.
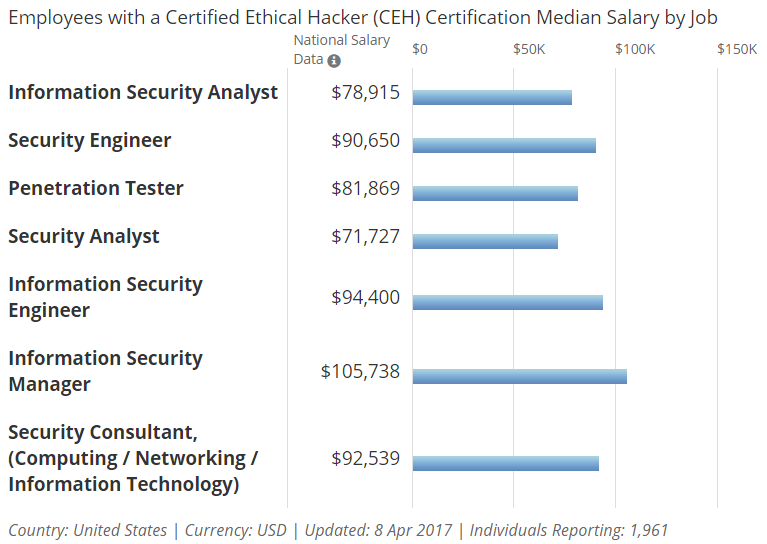
Here is a small overview of Ethical Hacker salaries depending on their skillsets:
To become an ethical hacker, you will mostly need technical skills. Some of them are listed here:
Also, these additional soft skills can be a big help as well:
Hacking can be used for good, or for bad. The name “Ethical Hacker” has meaning. It demands you to be abiding by your own hacking ethics.
Otherwise, an ethical hacker’s demand in the industry is huge. All you need to do is get your CertifiedEthical Hacker certification, and your career is future proof!
Confused about our certifications?
Let Our Advisor Guide You